Be exposed much of the day to devices with almost permanent internet connection may be a risk to the security of our information, which we have even seen as the same Mark Zuckerberg cover the webcam and microphone of your laptop with tape; here we could enter into the debate “I have nothing to hide”, however many believe that the Internet disconnect the risk is over. Today we will see that it is not.
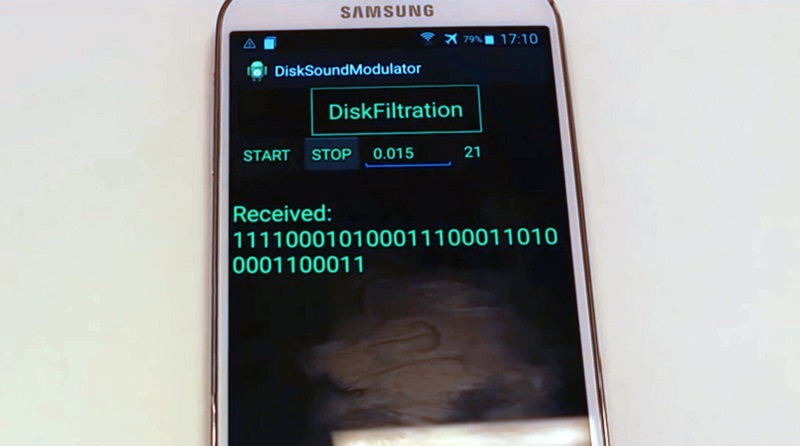
Today has come to light a method developed by security researchers at Ben-Gurion University in Israel who is accessing data from a hard disk by means of acoustic signals emitted, i.e. not any need remote connection, just listen to the actuator to write and read data, and a series of requirements.

Hacking based on the sounds of hard disk
The method is called DiskFiltration and consists of a series of complex steps that truth are difficult to carry out by an ordinary person, however it works and that’s the interesting part of all this, as many believe the hacks occur only when we are connected to the Internet.
The first thing you need is to install malware on the computer, which will be in charge of giving us control actuator hard disk, which moves forward and backward when he writes and reads data caused the presence of different sounds. Having control of the sounds emitted by the controller the next step is to have a device capable of decrypting, in this case a smartphone.
You may also like to read another article on Web2GB: The FBI could be authorized to hack devices almost anywhere in the world
This application works less than two meters away and is limited to a slow reading speed of only 180 bits per minute , so it would take about 25 minutes to break an encryption key RSA 4096 bits. Note that the method does not work because SSDs have no mechanical parts.
Of course the method and its implementation are very impractical, as it would need to have privileged access to the computer you want to hack, besides being close to hear the sounds of the hard disk, which is further complicated if there is presence of fans or external noise affecting listening. However the point is that our data demonstrate are exposed to various leaks that do not necessarily have to do with remote connections.
