In 2025, businesses soar through the cloud, embracing its agility and scalability. Yet, beneath this digital freedom lurks a growing menace: cyber threats targeting cloud applications. As a former IT consultant, I’ve seen companies scramble after breaches, losing trust and revenue. Key insights on cloud application security reveal how to protect these vital systems. This article dives into the evolving landscape of cloud app protection, blending storytelling with actionable strategies. From AI-driven defenses to human errors, we’ll explore what keeps security teams awake at night. Join me on this journey to uncover how businesses can fortify their cloud environments, ensuring innovation doesn’t come at the cost of safety.
The Rising Tide of Cloud Threats
Cloud applications power modern businesses, from startups to global enterprises. However, their accessibility makes them prime targets for cybercriminals. In 2024, cloud-based systems faced 47% of all data breaches, a 5% jump from the previous year, according to Check Point Research Check Point Research. My first encounter with a cloud breach was in 2022, when a client’s misconfigured server exposed sensitive customer data. The fallout was swift—reputational damage and costly recovery.
Attackers exploit vulnerabilities like stolen credentials, which caused 16% of breaches in 2024. Additionally, ransomware surged by 126% in Q1 2025, per SentinelOne SentinelOne. These threats evolve rapidly, targeting APIs and serverless environments. Therefore, understanding the threat landscape is critical. Businesses must stay vigilant, as attackers leverage AI for sophisticated phishing, making traditional defenses obsolete.
Why Misconfigurations Haunt Cloud Security
Misconfigurations remain the top vulnerability in cloud apps. In 2024, 31% of cloud breaches stemmed from human error or misconfigured resources. I once helped a startup fix a misconfigured AWS bucket that exposed user data. The oversight was simple—a public access setting left unchecked—but the consequences were dire.
Moreover, misconfigurations often arise from rushed deployments or lack of expertise. Tools like AWS Config or Cloud Security Posture Management (CSPM) systems can automate checks, yet many teams skip them. Consequently, vulnerabilities persist, inviting attacks. To combat this, businesses must prioritize training and automated tools. Regular audits and clear policies can prevent costly mistakes, ensuring apps stay secure.
Here are common misconfiguration mistakes to avoid:
- Unsecured APIs: Weak authentication exposes endpoints.
- Overprivileged accounts: Excessive permissions invite abuse.
- Public storage buckets: Unchecked settings leak data.
AI: The Double-Edged Sword in Security
Artificial intelligence reshapes cloud app protection, offering both promise and peril. AI-driven tools, like Amazon GuardDuty, detect threats by analyzing vast datasets in real time. A 2024 Cloud Security Alliance survey found 63% of security professionals believe AI enhances threat detection Cloud Security Alliance. I recall a project where AI flagged unusual login patterns, stopping a breach before it escalated.
However, attackers also wield AI, crafting convincing deepfake phishing campaigns. These attacks trick even cautious employees, amplifying risks. Therefore, businesses must balance AI’s benefits with vigilance. Integrating AI with zero-trust models ensures every user and device is verified, reducing breach risks. As AI evolves, staying ahead requires constant adaptation and employee training.
Zero Trust: Redefining Access Control
Zero-trust architecture is no longer optional—it’s essential. In 2025, 81% of organizations have adopted zero trust, per TechMagic TechMagic. This approach assumes no user or device is inherently trustworthy. I once worked with a firm that ignored zero trust, only to suffer a breach from an unverified internal account.
Furthermore, zero trust enforces strict authentication for every API call and user request. It minimizes attack surfaces, especially in multi-cloud setups. For instance, role-based access controls in Kubernetes prevent unauthorized access. Consequently, adopting zero trust strengthens defenses against internal and external threats. Businesses should implement multi-factor authentication (MFA) and least-privilege policies to lock down cloud apps.
Zero Trust Best Practices:
- Enforce MFA across all accounts.
- Use role-based access controls.
- Monitor all API calls continuously.
The Power of Proactive Security Posture
Reactive security no longer suffices in 2025. Only 21% of companies prioritize preventative measures, leaving most vulnerable to post-breach chaos. My experience with a retail client taught me this lesson. Their delayed response to a ransomware attack cost millions in downtime. Proactive strategies, like continuous monitoring, could have saved them.
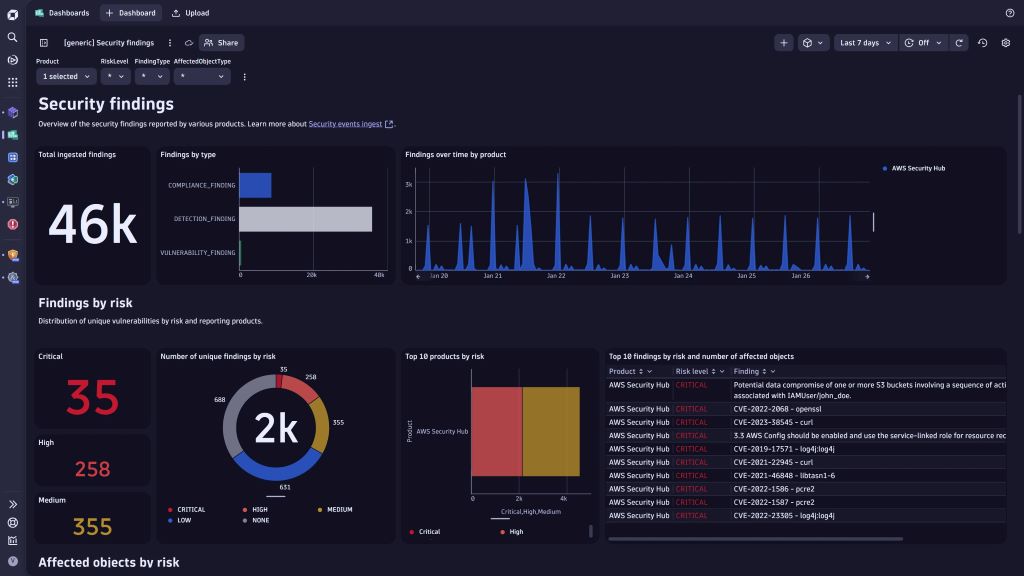
Additionally, Cloud Security Posture Management (CSPM) tools automate compliance checks and vulnerability scans. They provide real-time insights, catching issues before exploitation. For example, AWS Security Hub alerts teams to misconfigurations instantly. Therefore, shifting to proactive defenses reduces risks and enhances resilience. Investing in automation and regular audits is non-negotiable for secure cloud apps.
Proactive Security Checklist:
- Automate compliance checks: Use CSPM for real-time monitoring.
- Conduct regular audits: Identify vulnerabilities early.
- Train staff: Foster a security-first culture.
Encryption: The Bedrock of Data Protection
Encryption safeguards cloud data, both at rest and in transit. In 2025, quantum-resistant encryption gains traction as quantum computing looms. AWS Key Management Service (KMS) simplifies key management, ensuring robust protection. I once helped a healthcare client encrypt patient data, preventing a potential HIPAA violation.
Moreover, homomorphic encryption allows computations on encrypted data without decryption, boosting privacy. However, many businesses overlook encryption due to complexity or cost. This oversight invites breaches, as unencrypted data is an easy target. Therefore, adopting advanced encryption and integrating it into workflows is critical for cloud app security.
Encryption Tips:
- Use quantum-resistant algorithms.
- Leverage managed key services.
- Encrypt data at all stages.
Navigating Multi-Cloud Complexity
Multi-cloud strategies dominate, with 78% of organizations using multiple providers in 2025. This flexibility optimizes performance but complicates security. I advised a company juggling AWS and Azure, struggling with inconsistent policies. Unified platforms, like Fortinet’s Lacework, streamline management across clouds.
Additionally, multi-cloud setups increase misconfiguration risks due to varying interfaces. Cybersecurity mesh architecture offers a decentralized solution, enhancing visibility. Consequently, businesses must centralize oversight while allowing team autonomy. Tools like CloudGuard provide comprehensive protection, reducing gaps in multi-cloud environments.
Multi-Cloud Security Strategies:
- Centralize policy management.
- Use cybersecurity mesh for visibility.
- Standardize configurations across providers.
The Human Factor: Training and Awareness
Technology alone can’t secure cloud apps—humans are the weakest link. In 2025, 83% of breaches involve human error, per the Cloud Security Alliance. I’ve seen employees click phishing links, unaware of the risks. Training programs and phishing drills can transform staff into a human firewall.
Furthermore, fostering a security-first culture encourages vigilance. Gamification, like rewarding employees for spotting threats, boosts engagement. Therefore, investing in training reduces costly mistakes. Regular workshops and clear policies empower teams to protect cloud applications effectively.
Training Tips:
- Conduct monthly phishing drills.
- Reward proactive security behaviors.
- Simplify policies for clarity.
Visualizing Cloud Security Risks
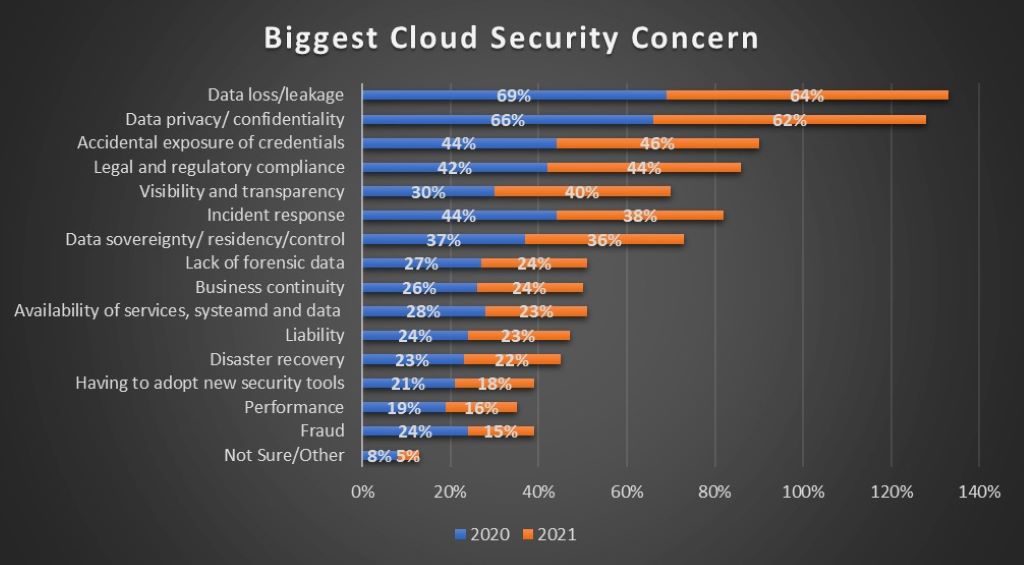
Understanding risks requires clear visualization. Below is a chart highlighting common cloud security threats in 2025, based on recent data:
| Threat Type | Percentage of Breaches | Primary Cause |
| Misconfigurations | 31% | Human error |
| Credential-based Attacks | 16% | Stolen credentials |
| Ransomware | 25% | Advanced phishing |
| API Vulnerabilities | 12% | Weak authentication |
This chart underscores the need for targeted defenses. Tools like CSPM and zero trust can mitigate these risks effectively.
Conclusion: Fortifying the Cloud Future
The cloud revolutionizes business, but key insights on cloud application security highlight the need for vigilance. From AI-driven defenses to zero trust, proactive strategies are essential. My journey through IT security taught me that preparation trumps reaction. By embracing encryption, training, and automation, businesses can thrive securely. What’s your take on cloud security? Share your thoughts or experiences below, and let’s keep the conversation going!
FAQs
What are the top cloud security threats in 2025?
Misconfigurations, ransomware, and credential-based attacks lead, driven by human error and sophisticated AI-driven phishing.
How does zero trust enhance cloud app security?
Zero trust verifies every user and device, reducing unauthorized access risks in dynamic cloud environments.
Why is encryption critical for cloud applications?
Encryption protects data at rest and in transit, preventing breaches and ensuring compliance with regulations.
How can businesses prevent cloud misconfigurations?
Use CSPM tools, conduct regular audits, and train staff to ensure secure configurations across platforms.
What role does AI play in cloud security?
AI enhances threat detection but also empowers attackers, requiring balanced defenses like zero trust.
Read More:
Seven apps to create a timelapse video on Android